- Installing custom themes on 6.60 firmware for dummies (cxmb plugin + ctf themes). My third tutorial. This time I'll show you how to install awesome looking.ctf themes on 6.60 cfw PSP. Click here for tutorial. This thread is archived. New comments cannot be posted and votes cannot be cast.
- One piece: unlimited world red ps3 one piece pirate warriors; pes 2014 - pro evolution soccer; pes 2016 ps3 playstation 3 promotion; playstation 3 super slim 500 gb black ประกันศูนย์ไทย 1 ปี playstation 3 super slim 500 gb white ประกันศูนย์ไทย 1 ปี playstation eye.

Name Date Format Location Weight Notes; WeCTF 2021: 19 June, 17:00 UTC — 20 June 2021, 17:00 UTC: Jeopardy: On-line 25.00: 0 teams will participate; Pwn2Win CTF 2021: 28 May, 16:37 UTC — 30 May 2021, 16:37 UTC. Ctf: Download File. Powered by Create your own unique website with customizable templates.
6.60 Ctf Themes
pass:http://www.nicoblog-games.com

Ctf Themes Psp Unlimited Apk
3. Copy the CTF file to your PSP Theme folder, example: I:PSPTHEME
4. Download CXMB plugin, extract it, and copy the cxmb folder to the root of your memory stick.
Download Psp Themes
ms0:/cxmb/cxmb.prx 1
ef0:/cxmb/cxmb.prx 1
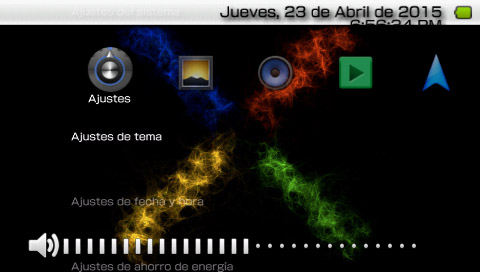
7. Go to Settings -> Theme Settings -> Theme
And select the Theme you want.
I participated at the HackIT 2017 CTF with team sec0d, and we finished first. As requested by some other teams, here’s a write-up for the Web200 CTF challenge of HackIT 2017.
Introduction
The application seems pretty straightforward, we can register with an username, a password, and a secret. The goal of the challenge is to recover the secret of an administrator.
Solution
Checking the source of the profile page, we can see some interesting information:
First, the secret is shown in an input tag. We can see that we can edit part of our profile as well by using edit.php. This page will edit the “about” field of our user.We can also see that there is an administrator function commented in the html, hinting us of a potential XSS or similar attack, as the administrator will have a list of updated status in his dashboard.
XSS tentatives will be proven to be unsuccessful, as we do not have access to the < and > characters and we are not in an attribute. A bbcode function is however enabled on the application, allowing us to input interesting data, for example, [code]Message[/code] will be translated to <pre>Message</pre>. Testing all possible bbcodes, one, in particular will be interesting to us, color.
The color bbcode injected, we can see the result:
As shown in the screenshot, the parameter “test” is inserted inside a style tag, and since other characters are not correctly filtered, we can do a CSS injection:
Using that as input will change the background image of some HTML tags and generate a request to our website.
Now that we know we can inject CSS and that there is effectively a bot running on the app, we can try to recover the input value using attribute selector in CSS:
This will check if the value of the input starts with h4ck1t, the i modifier after the selector is there to be case insensitive, since the page will lowercase all input value sent.
After sending that, we got our response, the flag format being h4ck1t{flag}, we can confirm that we only have to automate the attack :)
The server and bot being somewhat unreliable, we had to try everything manually. On a stable challenge, this challenge could be solved using a loop checking the character one by one.
Usage: python web200.py 'h4ck1t{c...'
And finally, in our logs, after a little bit of guessing and a sleep() time of 10 seconds…
Bonus
After solving the challenge, a friend I did the CTF with told me there could be a faster solution than bruteforcing the characters ourselves, even on unreliable servers. It is possible to simply create a lot of selectors, like h4ck1t{[a-z0-9] and by sending one request, the server will answer us with one character.